I got recently a package of files found in a infected POS (POS hacked due to a weak rdp password)
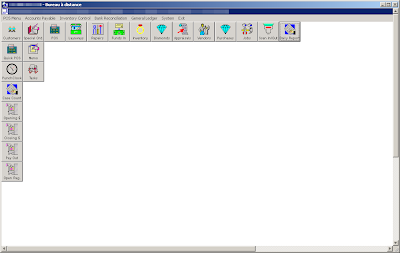
Interface of a compromised POS used by a jeweller:
out.exe is a Ardamax Keylogger (ardamax.com) and vui qua.exe is a SFX archive who display this picture when executed:
And drop Pefect Keylogger (blazingtools.com) behind.
"vui qua" might be a Vietnamese phrase which translated is "so funny".
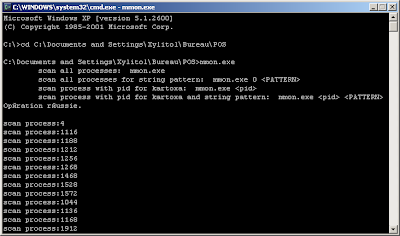
These two keyloggers are probably useless for the carder, the interesting file here is "mmon.exe" a ram scraper.
It scan each and every process looking for CC dumps thats been written to memory Track 1, 2.
If a Point Of Sale device is connected to the computer it will grab it's card data right away.
How? POS always use end to end encryption, the only place where it's not encrypted are inside the memory.
But.. the memory have limited storage so it overwrites the data all the time.
It's also a problem for mmon, because this crap have no loop feature and does not write inside a file.
POS Carders usually use better malware than this, but i got this so...
(mmon.exe, "Kartoxa" is probably the distorted version of the word "potato")
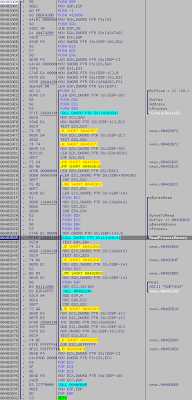
mmon scanning process.
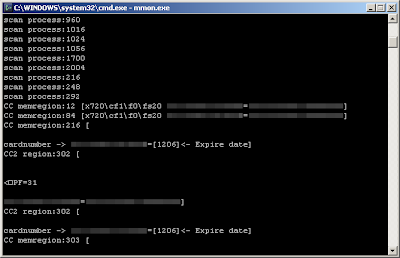
test of mmon with a valid track two in memory
When a dump is found, the program do nothing with it, it just display the stuff on console.
The bad guys just connect to the POS via RDP, get dumps via mmon and write them out on magnetic stripe with a card writer.
(MSR606 USB Magnetic Stripe Reader Writer/Encoder)
Then use an embosser to make imprinted numbers on the card.
(A DXR 70C embosser)
And it's ready to use... in USA (Type 101)
The ones we have in Europe are 201 cards (pin and chip)
101 only need to swipes the card in a store and the cashier checks the 4 last digits on the card if they are corect.
Carders also use printers like Fargo to make fake identities.
Anyway, a POS malware have a high price, it's not a business that everyone can do.




Let's go shopping!
ReplyDeleteCould you inform the MD5/ Virus total scan of these files?
ReplyDeleteThanks in advance!
from what I have heard, security on POS systems are really poor
ReplyDelete"Kartoxa" ))
ReplyDeleteyeah, that a very funny type of saying potato in russian )
out.exe: 1843B06D1C161B42A8D3794B6E1E02CE
ReplyDeletevui qua.exe: 3F85A322E587D125D51E743804A4742E
mmon.exe: 255DAA6722DE6AD03545070DFBEF3330
Kartoha is not potato. It is about "karton" (credit cards in russian carders slang.)
ReplyDeleteWhat kind of pos does that reflect on? Like the ones in wal mart? Those gray old crappy looking ones
ReplyDeleteHi, give me link for this soft
ReplyDeletesoraya bot dumps grabber ripper
ReplyDeletehe is a big big ripper here is proof
dr.dre@xampp.org.uk (13:39:00 23/07/2014)
im interested in soraya bot
dr.dre@xampp.org.uk (13:39:08 23/07/2014)
is it getting dumps ?
r0trteam (20:17:00 23/07/2014)
Yes
dr.dre@xampp.org.uk (20:45:13 23/07/2014)
how much is it
dr.dre@xampp.org.uk (20:45:14 23/07/2014)
add me pls
dr.dre@xampp.org.uk (20:45:27 23/07/2014)
tell me what it does
dr.dre@xampp.org.uk (20:45:33 23/07/2014)
any panel to test or review
dr.dre@xampp.org.uk (20:47:10 23/07/2014)
hello
dr.dre@xampp.org.uk (20:48:51 23/07/2014)
r0trteam (20:50:44 23/07/2014)
dr.dre@xampp.org.uk (20:51:11 23/07/2014)
im interested in soraya
r0trteam (20:51:35 23/07/2014)
Ok
r0trteam (20:51:40 23/07/2014)
core $50
dr.dre@xampp.org.uk (20:51:43 23/07/2014)
what is core
r0trteam (20:51:47 23/07/2014)
full plugins $200
dr.dre@xampp.org.uk (20:51:56 23/07/2014)
what is the purpose of it
r0trteam (20:52:01 23/07/2014)
core = only loader
dr.dre@xampp.org.uk (20:52:04 23/07/2014)
how good is it in victims pc
dr.dre@xampp.org.uk (20:52:09 23/07/2014)
what are the plugins
dr.dre@xampp.org.uk (20:52:20 23/07/2014)
is it getting dumps from pos is it mmon.exe or rdserv.exe ?
r0trteam (20:52:22 23/07/2014)
No formgrabber, No sock4, No Webinjects No tracks
dr.dre@xampp.org.uk (20:52:36 23/07/2014)
what crypter works with it
r0trteam (20:52:36 23/07/2014)