KINS is the acronyme for Kasper Internet Non-Security, the guys of RSA Security have made an article here: https://blogs.rsa.com/is-cybercrime-ready-to-crown-a-new-kins-inth3wild/
The advert was took on a (lame) forum know as 'verified', hread got removed later, as usual when they see that someone use their advert to blog.
I've read also the Fox-IT article about 'kins' but did they even know what they are talking about ?
The picture of the CNC just looks like a regular zeus with a bit of CSS work.. and the hashs didn't look like Zeus but also didn't look like the Kins i get..
"users of KINS have migrated to"
Interesting, that means KINS was something before what me and criminals call KINS now..
Small edit: and that was true and i was wrong, my apologies goes to Foxit guys.
I mean, if you look on underground forums, e.g: Darkode, exploit.in etc.. KINS stand for this modular alueron (even on verified or any other undergound boards)
i know i've wrong but what's can i say when most of peoples call this KINS so.. let's call this KINS even if it's not the good things to do.
No one (just S21 guys?) blogged about this variant.
After finally got KINS, i've sent it to RSA Security due to the weird article of Fox-It and also because i appreciate more the guys of RSA :) (and i know no one at Fox-It)
We have do a 'collab' analysis of the package.
The KINS 'leaked' package (not really 'leaked' for the moment but 'for sale') is composed of many folders like:
The folder source is half complete but we have already a good insight of what KINS do.
MS10-073 (win32k.sys KeyboardLayout vuln)
MS10-092 (Task Scheduler vuln)
Some files seem to come from the Carberp leaked archive, eg with the folder 'common':
VMProtect SDK:
KINS dll:
Many file names are evocative, KINS is basically: Zeus 2.0.8.9 + Power Loader 2.0 + SpyEye Plugins
And not like Citadel, KINS is almost 99% a "copy/past" of Zeus.
output (malware builder and dlls):
admindropper (Power Loader modified panel) aka 'A':
admincore (Zeus modified panel) aka 'B':
Builder folder is the first folder i've open:
KINS Builder 'Debug version'.
output:
Dropper.exe is detected as Alureon by Microsoft (Power Loader)
Bot32.dll is detected as EyeStye.plugin by Microsoft (SpyEye)
Bot64.dll is dected by just one antivirus (SUPERAntiSpyware) and the signature is generic (LOL!).
Bot32 is a Zeus bot, he have several strings related to SpyEye.
This is probably why Microsoft identify it as it.
"C:\Zeus projects\last\src_current\source\clientdll\spyeye_modules.cpp"
If you start it like this way:
rundll32.exe bot32.dll,ImageLoadNotifyRoutine
It start to write C:\debug.txt like zeus does when it starts in debug mode but then rundll exits and nothing happen.
When you inject it now, (inside iexplorer.exe for example) it grab datas and do the usual things Zeus do, no more no less.
And you can see/dump the base config from memory, it's easy to identify the drop zone and see webinjects.
well like Zeus huh ?
Original WebInject:
Here, the 'test' webinject do not work because ya.ru redirects to yandex.ru
KINS come also with a readMe, who explain you the life about Zeus webinjects and the package.
For the dropper well it's Alureon... MS10-073, MS10-092 injection of bot32.dll is working good.
If you want a reliable signature to identify KINS you can use Trojan:Win32/Alureon.GC of Microsoft.
During all the infection process, the dropper do several OutputDebugString making the routines identification relatively easy.
This KINS package seem more a test version not yet finished than a final package ready for customers.
For the x64 DLL of KINS and the x64 Dropper.... as i don't have this architecture i've not looked into thoses files.
After, why AV detections have vanished on the x64 versions... no idea.
Now for other files in the 'output' folder we have:
mod-killer.dll (kills SpyEye and Zeus based malware, e.g: Citadel, Ice9, Evolution...)
socks5Server32.dll (for do reverse connections through a proxy server, we have also socks5Server64.dll)
softwaregrabber.dll (Grab passwords,email,ftp,cookies,certs...)
those plugins remind you something ?
181.191.255.130 ~ AS52284 Panamaserver.com
Guess what's did you find on this IP... A VMProtect panel:
For Kins licenses ?
This is what i thought first but finally there is nothing interesting inside, it's more like a 'test' implantation.
There is also a CCGRAB panel (usually used in addition for SpyEye,Zeus,Citadel,IceIX):
Once again here, nothing interesting.
Just some details:
I got an interesting chat with him, and he confirmed my doubt about the leak of the non-finished product.
Some files are also hosted on this server and once again nothing interesting (wtf!):
grb32.dll > 0/46 (who pop-up alert window)
torrent.exe > 13/47 (is Cidox, not kins related)
Having a look on the folder 'admincore':
/theme/throbber.gif:
You probably guessed it from the folder structure, this is a Zeus control panel (with a slightly modification).
For information, here we have fixed the errors and translated the panel to English with the help of @Malwageddon.
This panel was only available in russian language and was also full of bugs (php errors everywhere)
Installer:
CP login:
Summary:
Jabber notifier:
config.php:
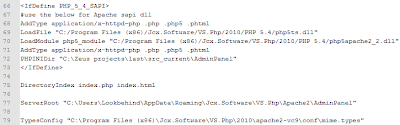
.httpd.conf:
"Lookbehind"
Install:
Stats:
Unlike the previous panel this one got really more code modifications.
As well as the curious title "bdrop v0.5 admin panel" instead of "PowerLoader v2.0"
See my post here for Power Loader: http://www.xylibox.com/2013/09/powerloader-20-alueron.html
Here again the panel was only in russian language and also full of bugs, the screenshot above was taken before our english translation.
Stats:
Bot list:
Tasks:
Add a task:
Files:
Add a file:
Settings:
Logs:
Something fun is the fact that everyone seem to have the same problem with KINS (broken panels) and all panels that we've dumped from malicious servers was similars with the same errors.
KINS on a malicious server with SSL for MitB webinject:
Zeus 2.0.9.15:
To finish... here are two demos, for those who haven't see them:
KINS Webinject in action: http://www.youtube.com/watch?v=4dL-WTyY6LM
Hacking KINS: http://www.youtube.com/watch?v=NVlqnKPZguw
AV guys: 90CAC1E1AD70EF5433B4E12EFCF78847

















































Awesome blog man!
ReplyDeleteVery nice blog, enjoyed reading it.
ReplyDeleteHowever I do not understand why, even though you state these types of things all over the article: 'And not like Citadel, KINS is almost 99% a "copy/past" of Zeus', you start the article of by saying that Fox it appears to not know what they're talking about... While their entire conclusion was that KINS is basically a ZeuS variant and not the insanely new banking threat RSA made it out to be.
Hi thanks,
DeleteWell, RSA was kinda wrong here too, that's right.
The first blog entry of RSA states what appear on the seller page, therefore they didn't know anything about it.
Although this is 99% a copy of a zeus.. KINS itself is a "modular" trojan based on Alureon.
And the 'Zeus' component is just a module which can be installed or not installed.
And even the Zeus itself it's not a regular Zeus like mentioned by Fox-it, but Zeus that was migrated to be a SpyEye module.
They said it was a ZeuS based kit and that it also features elements from SpyEye consistently saying it was a variant and not regular ZeuS so I still don't get the comments towards them.
ReplyDeleteThough this is a far more in depth analysis and made me understand it much more :-)
The only difference here is that what we know as KINS (i mean RSA and me) is actually Alureon...
DeleteAnd Fox-It identify it only as the Zeus component that comes with the whole-Kins..
I don't think that Fox-It were wrong classifying it as Zeus.. it's indeed almost 100% Zeus, but their report was not accurate in saying that it's only a zeus.
Why they think they know what kins is.. if everyone call what we analyzed kins..
Maybe there are 2 kins that are not related one to another..
It would be cool if a Fox-It guys can explain.
the most common problem each vendor name there samples $random it's also for that their 'zeusVM' don't match with our 'PowerZeus'
DeleteIntresting analysis,
ReplyDeleteA new malware that have nothing new. combine best parts from top malwares trying to be a new king in malware world and all this was made by a phD in the name of science
K.I.N.S can't working with chrome x32/x64?
ReplyDeleteUsers in USSR countries will not be infected by KINS[1] – a feature that was first introduced by Citadel in January 2012.
ReplyDeletereal?
Sorry just got to ask. Whats the name of the artist/track playing in the second video? :)
ReplyDeleteAs always awesome work brother!
ReplyDeleteI love reading your blogs, i learn alot frm your works. Computer world is safe because of kool researchers like u.
ReplyDeleteSo... where to buy this soft?
ReplyDelete