Not really hard to identify it.
Brontok.A was built with Visual Basic and use the packer: MEW (By NorthFox/HCC)
Copies itself to the user's application data directory and then in Windows.
with various name like: winlogon.exe, inetinfo.exe, smss.exe, csrss.exe, lsass.exe, svchost.exe etc..
not only in '.exe' in .src, .com, .pif and more extension in more directories
The worm try to navigate to:
http://www.geocities.com/stabro7ok/BrontokInf8.txt
http://www.geocities.com/stabro7ok/Bron-ID8.txt
And then, replace the data contained in drivers/etc/hosts by BrontokInf8.txt
A file called 'about.Brontok.A.html' was created in the folder 'My Pictures':
my documents... .exe :)

regedit was disabled
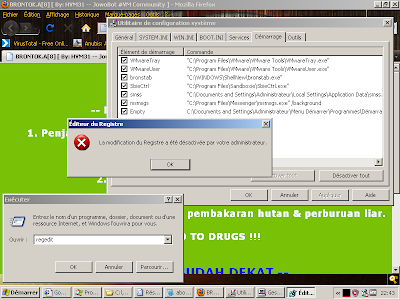
when you try to open cmd or when some word (like: REGISTRY) was detected on the handle of the curent open windows, Brontok will reboot your computer
Brontok launch ping flood attack on two websites
playboy.com:

And israel.gov.il:

Propagation was done by e-mail.
Brontok, search for e-mail addresses in your pc, and when found something use his own smtp engine for send a malicious mail
This worm was found in 2006, and actually detected by most anti-virus software
how my friend got infected... that a good question.
final word:




No comments:
Post a Comment