
I received several questions about previously posted MBRLock, the idea here to resume all: a tiny tutorial for pwned these lockers.
Firstly get infected (lol) you have two options, browsing a fake porn site and get exe or visit an infected webpage who lead to MBRlock execution.
The xxxvideo.avi.exe file have generally a ~61Kb size and most of time use a VB crypter.
It spawns new copy of process, decrypts data and writes them to new process ImageBaseAddress and then resumes main thread.
A quick way to unpack it is to set breaks on CreateProcess/WriteProcessMemory, but here the unpacking is not really important (We want just the MBR right?)
A fast way is to use HideToolz by Fyyre and enable the reboot protection, then you can infect your machine, HideToolz will block ExitWindowsEx done by the MBRLock.
The MBR is infected... what's now ?
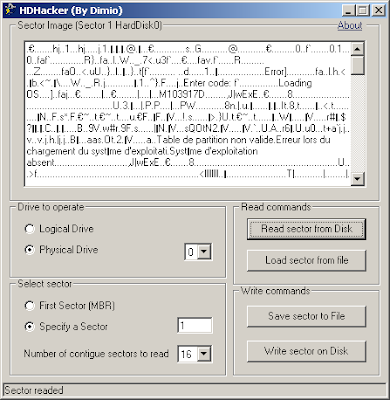
For make a dump personally I know two way: Hiew and HDHacker.
HDHacker is really handy:
Hiew is fastest (and used by most of malware researcher?)
For make a dump with Hiew, load it like this: hiew32 \\.\PhysicalDrive0
Then in hex mode press * for select the infected block and * again for finish,
Then, F2 to save the dump.
Now we have a copy of our infected MBR
To debug it, we will use IDA Pro, but firstly you need the good packages.
- Bochs v2.4.6 (you can use a newer version if you want but IDA Team doesn't recommend after v2.6.6)
- Python 2.7
- IDAPython
- MBR package of Elias
Now.. install 'em all.
Drop IDAPython folders into good IDA install dirs
Make your bochs image with bximage.exe, hd, flat, 10
Then build your image file with "mbr.py update"
Edit the bochsrc file of Elias to fix the directories lines and voila !
If you use another version than v2.4.6, some parameters may appear deprecated from the bochsrc file.
vga_update_interval: 150000 => vga: update_freq=60
keyboard: serial_delay=250, paste_delay=100000, type=mf
or well, just figure it out by reading the docs :)
Drag 'n' drop your bochsrc file on IDA, and you can start to debug, if everything load properly :þ
From command line if you prefer debugging directly:
idaq -c -A -OIDAPython:mbr.py bochsrc
ren bochsrc.idb mbr.idb
idaq -rbochs mbr.idb
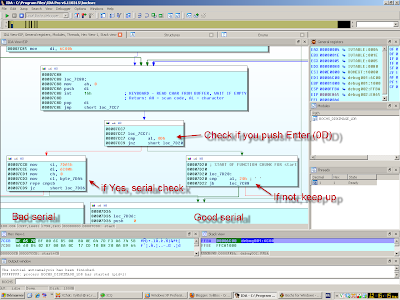
For do it fast with these lame lockers, here is the interesting code inside the bootloader:
Nj0y ~
As a tutorial, special hello and thanks to: Fyyre, EP_X0FF, Corkami, Hex-Rays guys.










Thanks, it was a great read. any chance I could get a copy of the exe?
ReplyDeleteSend me a mail at xylitol@malwareint.com and i will reply you with the sample in attach.
ReplyDeleteHi Steve, can i aso get a copy of the exe file, ive sent u an email in regards, thanx
Deletenice post man. btw, there is a supposed-to-be-censored part in image 2.
ReplyDeleteI've leaved the banner, it's not 'hardcore' like thumbles
ReplyDeleteIsn't fastest add to mbr.py a simple MBR dumper?
ReplyDeletefile("c:\\mbr.bin", "wb").write(file(r"\\.\PhysicalDrive0","rb").read(0x200))
Nice post, thanks!
How are you ENABLED registers IVT for Debuggin in IDA ???
ReplyDelete