I got the idea to make my stats, so i've requested a database copy (just the part about my submissions) I've wait and.. no answer.
Hmm alright, I've coded my tool for grab datas and export the shit in Excel :)
For don't make this post looking empty, I will retrace also my past of 'xssboy'
xssed.com is an online vulnerability archive, the largest on-line database of websites vulnerable to cross site scripting attacks.
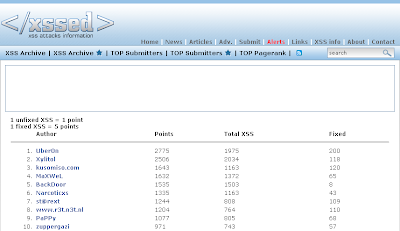
I've found XSSed in December 2007 and my period of high activity was in 2008/2009 to finally be part of the top.
Overall ranking:
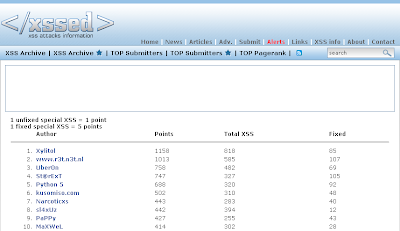
Special ranking (Governement/International etc...):
My ratio:
XSSed publishing activities:
I've stopped to submit since a long time... but the XSSed staff keep to add my stuff.
Publishing a 2008 xss in 2011 (I wonder what's my amount of not yet validated stuff):
My types of submissions:
I've made me one rule: no permanent XSS.
And also some 'special' submit like:
Who required staff intervention to make the mirror valid (adding the source manually or a screenshot, like for facebook):
Top 20 XSSed TLD:
Parsed domains:
aero
af
al
am
ar
army.mil
at
au
be
bg
biz
bn
bo
br
by
ca
ch
ci
cl
cn
com
cy
cz
de
dk
edu
edu.au
edu.cn
edu.eg
edu.in
edu.my
edu.pe
edu.pl
edu.tw
es
eu
fi
fr
ge
gob.mx
gob.ve
gouv.fr
gouv.mc
gouv.qc.ca
gov
gov.al
gov.ar
gov.au
gov.az
gov.ba
gov.bb
gov.br
gov.bs
gov.cm
gov.cn
gov.co
gov.dz
gov.ge
gov.gh
gov.hk
gov.il
gov.in
gov.ir
gov.it
gov.kz
gov.lb
gov.lv
gov.ma
gov.mn
gov.mo
gov.mv
gov.ph
gov.pk
gov.pl
gov.ru
gov.sa
gov.tn
gov.tr
gov.tw
gov.ua
gov.uk
gov.uz
gov.vn
gov.yu
gov.za
gr
hk
hr
hu
id
ie
il
in
info
int
is
it
jp
kiev.ua
kr
kz
lu
lv
ma
md
mil
mil.al
mil.gr
mil.id
mil.kr
mn
mobi
mt
mx
my
name
nasa.gov
navy.mil
net
nih.gov
nl
no
nz
org
pa
pe
pl
pro
pt
ro
ru
sa
sc
se
si
st
su
sv
th
tk
to
travel
tv
tw
ua
ug
uk
us
ws
yu
za
af
al
am
ar
army.mil
at
au
be
bg
biz
bn
bo
br
by
ca
ch
ci
cl
cn
com
cy
cz
de
dk
edu
edu.au
edu.cn
edu.eg
edu.in
edu.my
edu.pe
edu.pl
edu.tw
es
eu
fi
fr
ge
gob.mx
gob.ve
gouv.fr
gouv.mc
gouv.qc.ca
gov
gov.al
gov.ar
gov.au
gov.az
gov.ba
gov.bb
gov.br
gov.bs
gov.cm
gov.cn
gov.co
gov.dz
gov.ge
gov.gh
gov.hk
gov.il
gov.in
gov.ir
gov.it
gov.kz
gov.lb
gov.lv
gov.ma
gov.mn
gov.mo
gov.mv
gov.ph
gov.pk
gov.pl
gov.ru
gov.sa
gov.tn
gov.tr
gov.tw
gov.ua
gov.uk
gov.uz
gov.vn
gov.yu
gov.za
gr
hk
hr
hu
id
ie
il
in
info
int
is
it
jp
kiev.ua
kr
kz
lu
lv
ma
md
mil
mil.al
mil.gr
mil.id
mil.kr
mn
mobi
mt
mx
my
name
nasa.gov
navy.mil
net
nih.gov
nl
no
nz
org
pa
pe
pl
pro
pt
ro
ru
sa
sc
se
si
st
su
sv
th
tk
to
travel
tv
tw
ua
ug
uk
us
ws
yu
za
To find vulnerabilities I've mainly searched by thematic (TDL/Topicality) like this:
And later i've started to automate my xss searching.
I've coded my own tools (and released them few months after)
XSS Scanner (2008): My first scanner, released for Halloween on a underground forum.
Lame crap coded in two mins:
Tiny XSS Scanner (2009): More stable/clean and released with the source code.
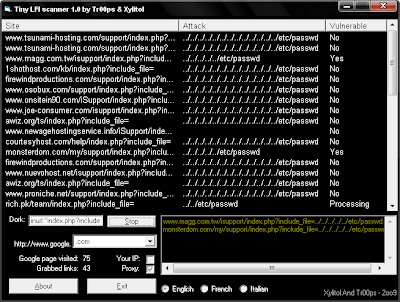
Tiny LFI Scanner (2009) Nothing related with XSS vulns, my mate tr00ps just joined the festivity
I've also made two papers about the cross, published firstly on Milw0rm, one of them was released later on "50-1337" (a French ezine)
Before the mag we have made (p3lo and me) the Attack-Vector project.
I've also published some security advisories during the time of xssing.com.
And one 'PoC pack' targeting Google.
In this demo (by p3lo) technic employed by the attacker will be the MITM proxy keylogger.
An XSS is dangerous yeah.. what's about redirect vulnerability?
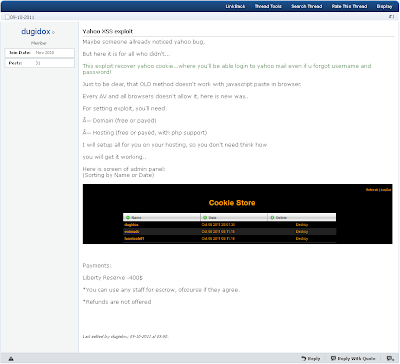
A guys selling xss vulnerability and panel for Yahoo:
Similar to this, i've also made my ugly cookie panel and beta-tested a javascript Shell made by a friend:
Like that i've started to derivate on browser vulnerabilities, playing with BEeF etc...
To finish, some noise:
Google accounts SSL login page suffers from highly critical XSS:
Five Sun.com XSS flaws in the SSL user login page:
Skype.com SSL powered support page vulnerable to XSS:
F-Secure.com vulnerable to cross-site scripting:
New HSBC and Barclays bank XSS and open redirect bugs:
I've never asked a reward.
On the past and like today: i do it for fun, not for profit.
btw il fallait absolument que je te chambre Xartrick, donc voilà:
<+Xartrick_> Xylitol > Chez EA Games, c'est des brèles, j'ai envoyé un mail il y a quelques mois pour une XSS, toujours pas fixed ...
<+Hydraze> hahahahaha
<+Hydraze> xss boy
<+Xylitol> xss boy
<+Horgh> !xartrick
<+Xyl{vps}> alert(1)
<+Xartrick_> sayé j'en prend pour mon grade.
<+Hydraze> hahahahaha
<+Hydraze> xss boy
<+Xylitol> xss boy
<+Horgh> !xartrick
<+Xyl{vps}> alert(1)
<+Xartrick_> sayé j'en prend pour mon grade.





















Just wondering how many of these you actually attempted to responsibly disclose before just tossing the vulns up on xssed. Seems a bit irresponsible...
ReplyDeleteResponsibly disclose.. none of them (clearly)
ReplyDeleteEven if I've wrote alot of mails (I even coded my tool for send mail directly with 'pre-made' dialog regarding the bugs and how to fix it)
When I became aware of certain things about how my submissions can be dangerous, I've stopped.
It's my past, I've made mistakes and also assumed them.