
I received a mail with an interesting stealer, thanks Raoul.
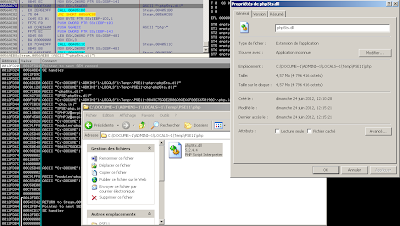
A fake Steam login who have a size of 6Mb, but why the size is so huge ?
Because they drop the PHP5 engine and load the script.
Here is a picture of the routine:
Create the file "php5ts.dll"
Write:
A ELF file is un-bunziped and loaded via the php:
Then delete
Loaded php5 dll:
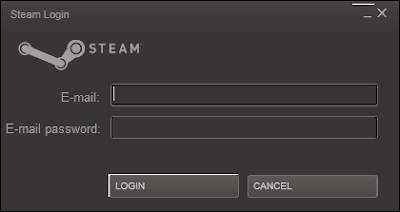
Loaded fake login:
After that you filled fields and send, the second windows is show:
With the SteamGuard protection hackers need now to have access on the E-mail adress used on Steam.
Datas are finally sent to the server after pushing the login button.
• dns: 1 ›› ip: 188.190.98.202 - adresse: HTTPZ.RU
To a fake gif image, i've already see that on Spyeye gates, with rules like this on htaccess:
AddType application/x-httpd-php .php .phtml .jpg .pdf
When datas are sent the following windows is show
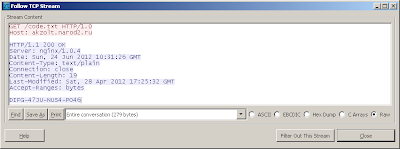
And then ask you a serial (???):
Who call another url:
If the code is good (DIFG-47JU-NUS4-PO46) the app just close, if the code is bad the app do nothing.
This Stealer is not new, according to VirusTotal the bzip2 compressed archive was first scanned the 2011/03/24.
Also if you have hl2:dm and want to play, add me :)
http://steamcommunity.com/id/temari
I 'm just back from Eurockéennes, it's for that these days i was not really online, here are two pics i've taken (Dionysos and Justice)













http://adadadassssadadad.co.cc/main.php?page=b120e4602a84d979
ReplyDeletehttp://adadadassssadadad.co.cc/bhstat.php?threadID=46&ruleID=0&key=701698bca5e8b0eb3c7ea955bb2e05b6
blackhole nigga
It's php devel studio. Script packed in overlay, gz format.
ReplyDeletehttp://develstudio.ru/